Fantastic Info About How To Detect Remote Access

Effortlessly access and manage your conversation history.
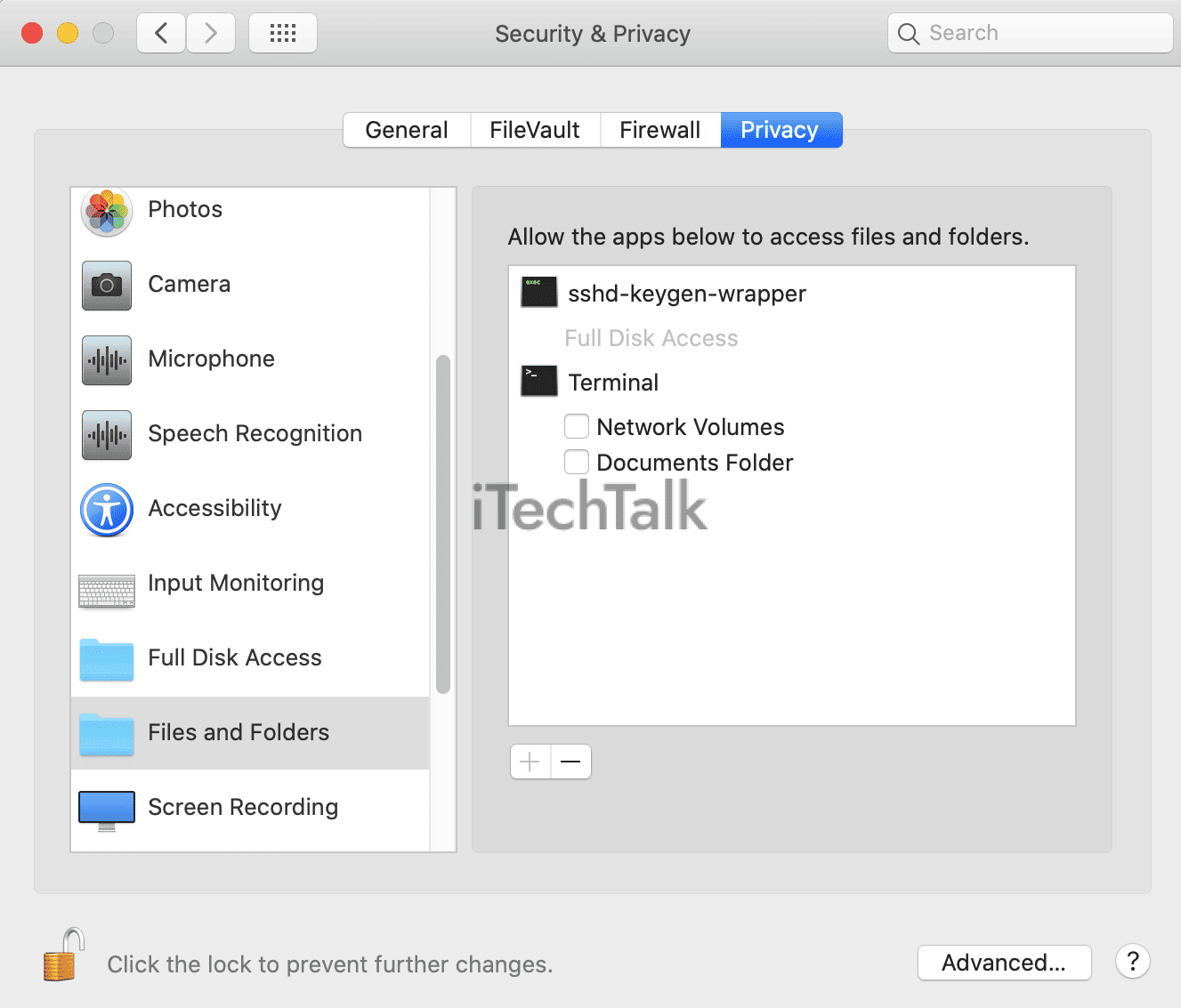
How to detect remote access. The rdp connection logs allow rds terminal servers administrators to get information about which users logged on to the server when a specific rdp user logged. Like legitimate software developers, malware developers code their software for a specific purpose. A remote access connection manager (rasman) is a service provided by windows that manages vpn connections between your computer.
There is no api or simple test a website can perform to know if there is a remote desktop involved. On your local windows pc: On your computer, open chrome.
A remote access trojan (rat) is a tool used. In the search box on the taskbar, type remote desktop connection, and then select remote desktop connection. If you suspect someone may be remotely viewing your session, you can run a packet sniffer like wireshark and see if there are any packets on ports used by vnc or rdp (remote.
What is remote desktop access. After accessing the setup wizard, an attacker will input new credentials to gain access to screen connect. In the address bar at the top, enter remotedesktop.google.com/access, and press enter.
Moreover, we are constantly discovering new tools for detecting social engineering technologies. Select the remote tab on the resulting utility, is the setting there to allow remote access disabled?
Efficient publicationretain your copyrightopen accesshigh editorial standards Find and run the quick assist app. Press win + r and then type in “ sysdm.cpl ” to open the system property.
Device parallel activity presence spotting. So they easy answer is no. I want to be able to.
Regularly, especially if you’re in an environment that frequently installs and tests new software. Before diving into detection methods, it’s essential to understand how remote access works. I am on a network from which any machine could do a remote desktop access to my windows machine using the tool (remote desktop connection).
We'll demonstrate how to lock down your computer, search for indications of remote connections and access, and avoid further invasions. How to remotely access a computer being able to control a computer remotely offers numerous possibilities for administrators as well as for employees. How to detect remote computer access (5 steps) 1.
Seamlessly move your chat data in and out of the platform. You may also have to update the app via the microsoft store. Doing so will write a new user database to a temporary.